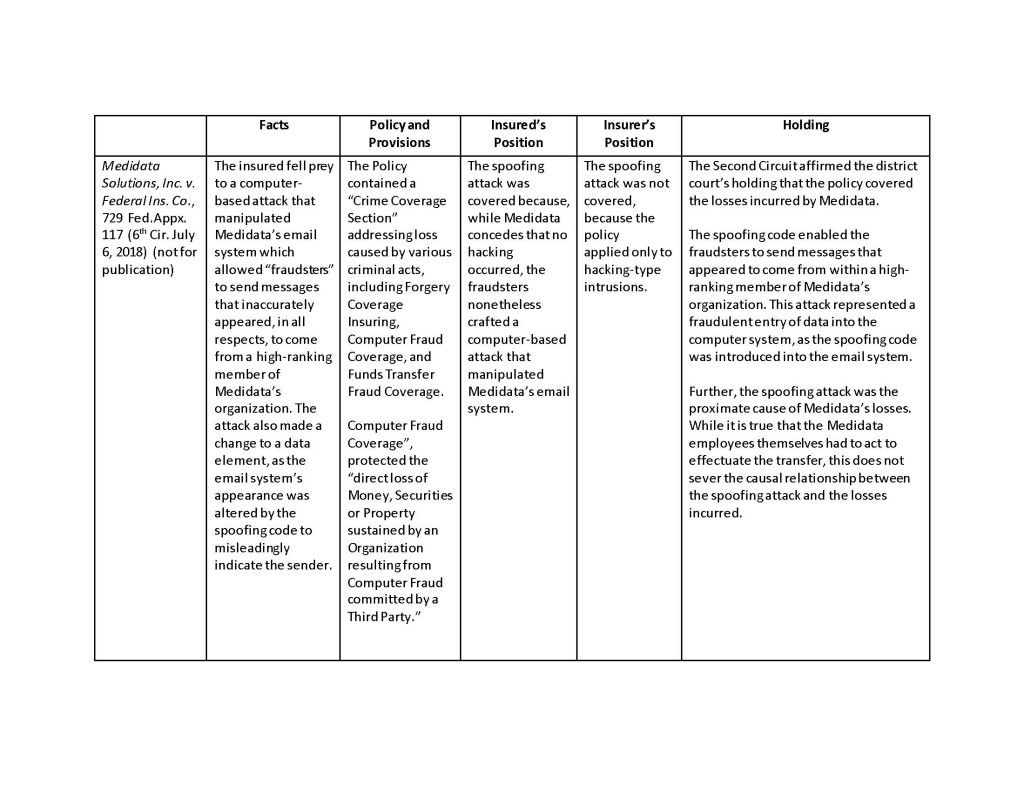
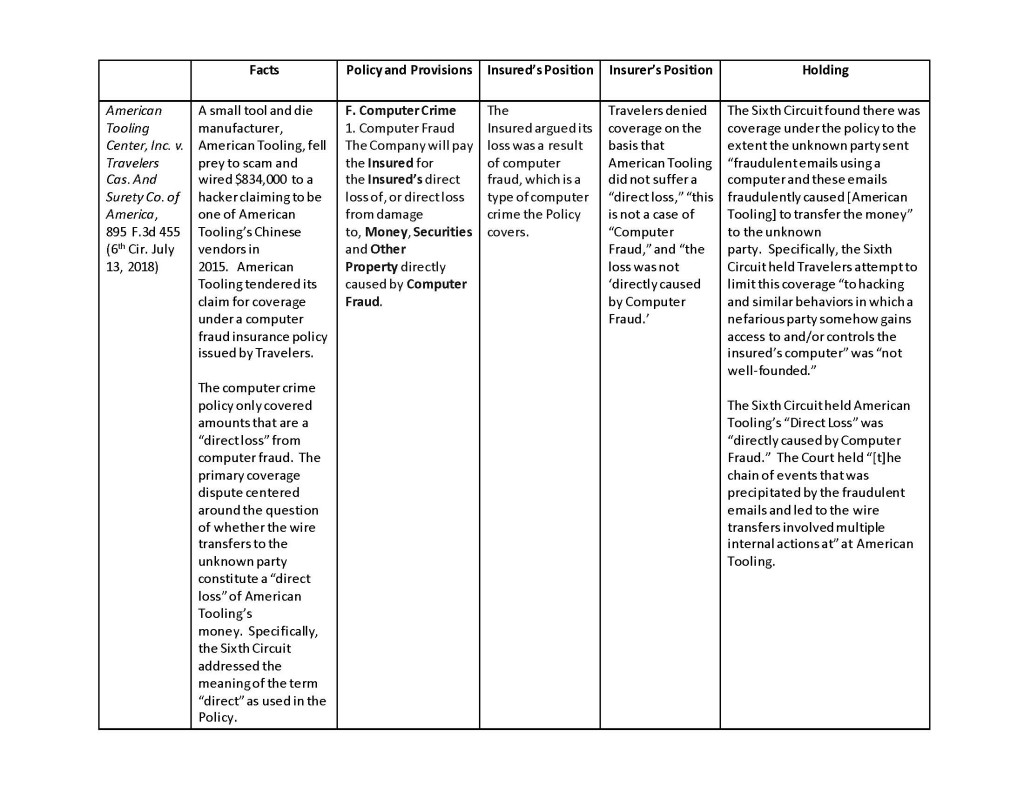
Courts have generally defined “spoofing” as “the practice of disguising a commercial e-mail to make the e-mail appear to come from an address from which it did not originate. Spoofing involves placing in the ‘from’ or ‘reply-to’ lines, or in other portions of e-mail messages, an email address other than the actual sender’s address, without the consent or authorization of the user of the e-mail address whose address is spoofed.” Kavaly v. eBay Inc., 245 F.R.D. 71, 91 n. 34 (E.D.N.Y 2007). This summer we have seen two important decisions related to whether “spoofing” incidents trigger coverage under computer crime insurance. First, on July 6, 2018, the Second Circuit in Medidata Solutions Inc. v. Fed. Ins. Co., 729 Fed. Appx. 117 (6th Cir. 2018), held a criminal’s manipulation of an insured’s email system triggered coverage under a computer crime policy. A week later, the Sixth Circuit in American Tooling Center, Inc. v. Travelers Cas. And Surety Co. of America, 895 F.3d 455 (6th Cir. July 13, 2018), held a spoofing scam that caused the insured to wire money to a fraudulent bank account also triggered coverage under a computer crime policy. These cases, which hinge on the use of a computer to commit fraud, are quickly becoming misunderstood as directly impacting the cyber insurance marketplace. [1]
The recent discussion surrounding these cases are confusing to the extent that courts have been analyzing computer crime coverage cases involving spoofing for quite some time. For example, in Apache Corp. v. Great American Ins. Co., 662 Fed. Appx. 252 (2016) (unpublished), the Federal Court for the Southern District of New York held there was no insurance coverage under a computer crime policy for a $2.4 million loss caused by an insured following a fraudulent website link to a fraudulent bank account. This fraud was put in motion with a phone call to the insured from a person claiming to be a vendor requesting payments be sent to a new bank account. The insured told the person that the change could not be made without a formal request on the vendor’s letterhead. A week later the insured received an email on what appeared to be the vendor’s letterhead providing information on the new bank account for money to be wired. The spoofing scheme worked and the insured did not figure out he was sending its payments to a fraudulent bank account until a significant amount of money had been sent.
The computer fraud policy at issue in Apache provided coverage “for loss of, and loss from damage to, money, securities and other property resulting directly from the use of any computer to fraudulently cause a transfer of that property….” The insured denied coverage for this claim because the “loss did not result directly from the use of a computer nor did the use of a computer cause the transfer of funds.” Ultimately, the Apache court found the use of email in the fraud scheme included telephone calls and forged letterhead was not covered under the computer fraud coverage because:
“[t]he email was part of the scheme; but, the email was merely incidental to the occurrence of the authorized transfer of money. To interpret the computer-fraud provision as reaching any fraudulent scheme in which an email communication was part of the process, would…convert the computer-fraud provision to one for general fraud.”
While the Apache court found a computer did not play a significant enough role in the spoofing scheme, this case demonstrates the significant precedent related to spoofing claims under computer fraud coverage. The most recent decisions out of the Second Circuit and Sixth Circuit merely build on this body of law in the following manner:
While the Second Circuit does not directly address the Apache decision in Medidata, the underlying decision of the District Court for the Southern District Court of New York rejected the insurer’s arguments based on the reasoning in Apache because “[t]he underlying fraud in Apache was achieved through a muddy chain of events.” See, Apache Inc. v. Fed. Ins. Co., 268 F. Supp. 3d 471 (2017). That is, the District Court held Apache is distinguishable because in addition to a computer, the criminals use phone calls, spoofed emails, and falsified documents. While this line of cases shows how courts address spoofing claims under computer crime policies, these cases provide no guidance in interpreting cyber policies that do not contain computer fraud coverage.
There are subtle differences between all the spoofing cases. However, the one consistent trait is there is computer fraud policy at issue rather than a cyber policy in each of these cases. This is not a point to be overlooked. For example, the Medidata court rejected the insurers position that the policy was limited “to only hacking-type intrusions.” Moreover, the insured conceded “that no hacking occurred.” On the other hand, most cyber policies are intended to only provide coverage for losses and liability caused by “hacking-type intrusions.” Consequently, the reach of these recent spoofing cases is limited to policies that provide computer fraud coverage.